
Free gift cards... but at what cost?
Introduction
My employer recently implemented a corporate rewards program. This program incentivizes employees by awarding them points that can be redeemed for valuable rewards such as gift cards.
One slow day in the Security Operations Centre (SOC), my manager issued a ‘call to pwn.’ Here’s the story of how I found a Business logic vulnerability that gave me “infinite money”
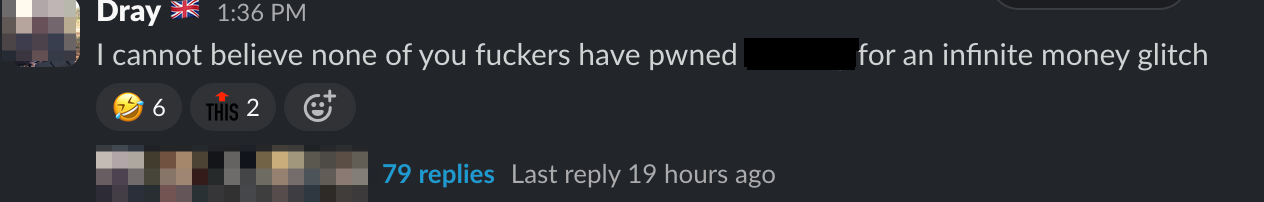
I have the pleasure of working with extremely intelligent people, with the above slack message coming in on my lunch break I knew my colleagues would already be trying to find bugs, unfortunately for them I am extremely competitive, I cut my lunch short with the intentions of finding a bug that will allow me to have “infinite money”
Initial Reconnaissance
Reconnaissance was an easy task with the self imposed scope of looking for bug that allows me to obtain infinite money that limited me to three main functions within the app:
- Send Points
- Receive Points
- Redeem Points
I began with reviewing how to redeem points. I made a test purchase while capturing the requests in burp, I attempted to manipulate the request by modifying values. All attempts were unsuccessful, The redeem portion of the app was more complex that I anticipated, With multiple failed attempts and my virtual funds running low I decided to move on.
Note: Changing the region of your account to the United States gave you different prices and quantities?
Sending/Receiving points required an additional person for testing, Thankfully Austin (@0xffaraday) volunteered.
We began sending points to each other. Any points sent publicly are viewable by all employees who are able to “add-on” with a comment which can include extra points
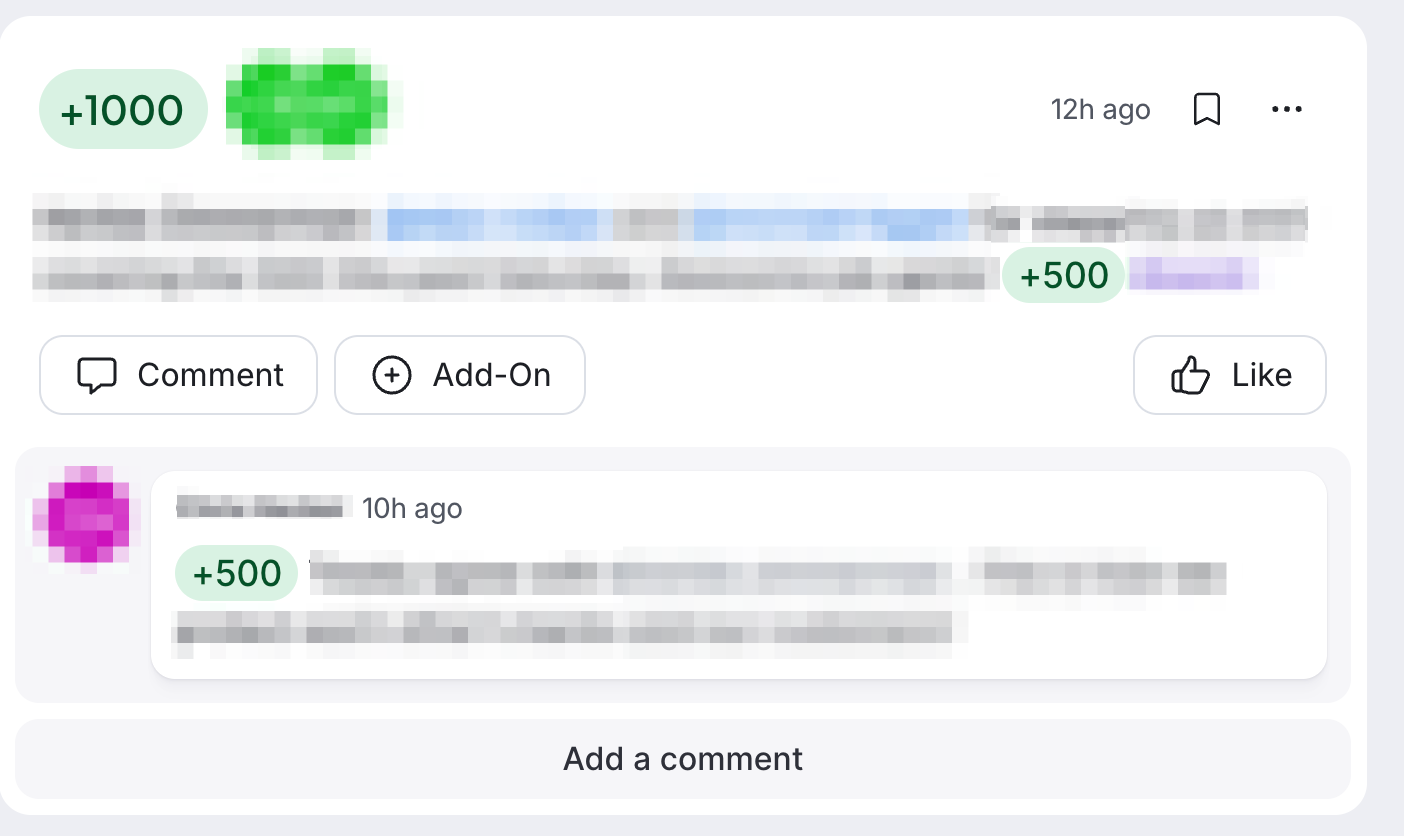 The posts in which the points were given allowed you to edit and delete comments within a 5 minute window, This also allowed you to edit the amount of points sent, These functions were looking promising.
The posts in which the points were given allowed you to edit and delete comments within a 5 minute window, This also allowed you to edit the amount of points sent, These functions were looking promising.
Discovery
I first began by sending points, then editing my comment to remove the points, just to see what would happen, surprisingly it worked but sadly the receiver did not keep the points after the edit but the sender did get their points back if the amount given was changed to zero, This was some pretty interesting behaviour and raised the question “What if I edit my points given, After you already buy something?”
Austin & I quickly jumped into a zoom call and began testing… A few moments it works! within under an hour and a half I had found got a working POC and answered the call to pwn
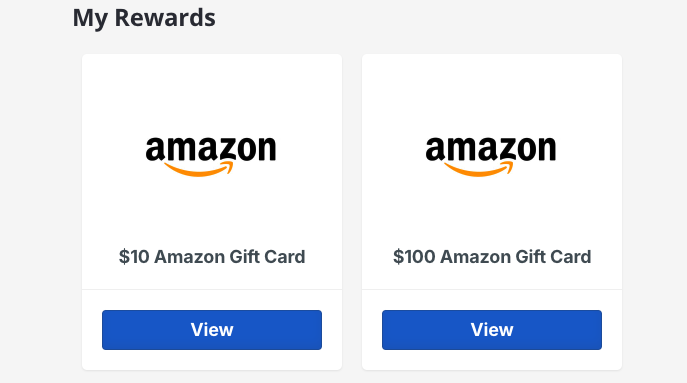 While I was busy celebrating, There was one problem we did not take into account the possibility of a negative account balance… I may have got a working POC but at the cost of sending Austin into virtual debt.
While I was busy celebrating, There was one problem we did not take into account the possibility of a negative account balance… I may have got a working POC but at the cost of sending Austin into virtual debt.
Disclosure
After disclosing to the vendor I was able to successfully bypass the patch by repeating the above bug by instead of editing my value to zero, I just deleted the child comment. This also worked if you deleted the parent comment but it had to have no points within the comment to work.
Now this was not the most technical bug or even impactful but I enjoyed the simplicity of this business logic bug.
Disclosure timeline
- 05/09/204 - Initial Discovery and Disclosure
- 06/09/2024 - Vendor requested meeting
- 11/09/2024 - Vendor confirmed Fix was in place
- 16/09/2024 - Found Bypass same bug but this time in the child comment
- 20/09/2024 - Fixed Bypass
Special thank you to Dray Agha (drayagha.uk) for the challenge and Austin Worline (@0xffaraday) for helping me test.