Introduction
Sometimes the most interesting research opportunities find you, not the other way around. While monitoring a public Discord server—a common meeting ground for low-skilled threat actors—we found an interesting claim. A user was boasting about finding an “unsecured government satellite” on Censys. As soon as we saw the associated web application, the application’s outdated design signaled its age That instant curiosity, that suspicion of what vulnerabilities might lie underneath, compelled us to investigate a discovery that, unbeknownst to the original poster, could have caused real damage.
Before proceeding, it is important to clarify the nature of our investigation. While we did not have explicit, written permission to test the security of this system, we proceeded with extreme caution and in good faith. This specific government body was observed to be publicly accepting bug reports, which we interpreted as a clear sign of their commitment to security. Our primary motivation was to understand what a malicious actor might be able to achieve, given that the application was being discussed in a public forum and could have been exposed to a potential attack. We took every precaution to avoid causing any disruption and committed to responsible disclosure as soon as we had sufficient evidence.
Initial Reconnaissance
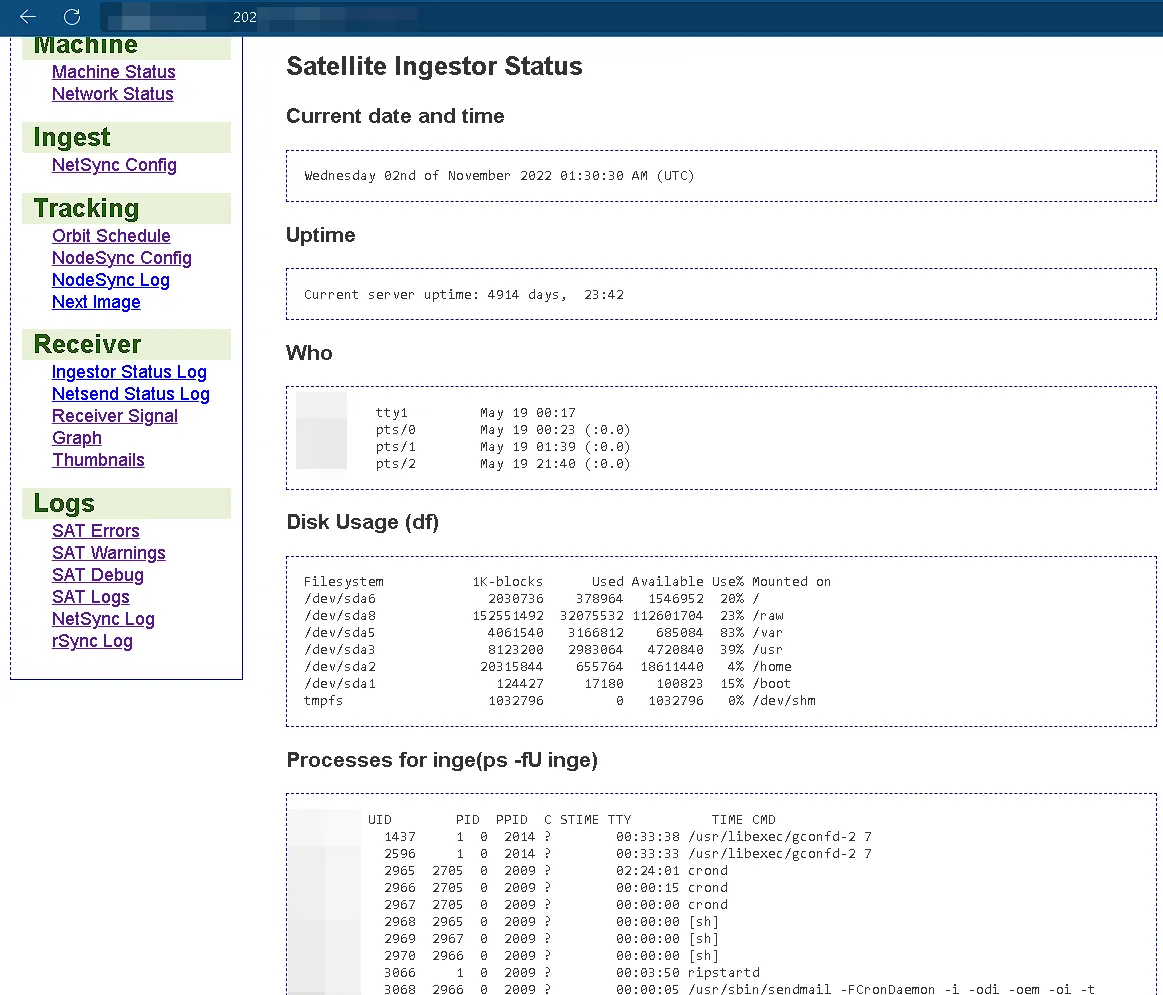
Our review of the web application didn’t immediately reveal a critical security flaw. Instead, it raised a more fundamental question: how was this data being displayed, and what process was running in the background to fetch these underlying system details? While information disclosure wasn’t the main vulnerability, it was our first major clue. It signaled that the application was interacting with the server in a way that it shouldn’t be, sparking our curiosity and pointing us toward a deeper issue.
Discovery
Our curiosity about the application’s backend paid off quickly. We began systematically testing the web application’s parameters, and it wasn’t long before we stumbled upon something promising: an f parameter. Our initial tests showed that this parameter allowed us to include local files from the web server.
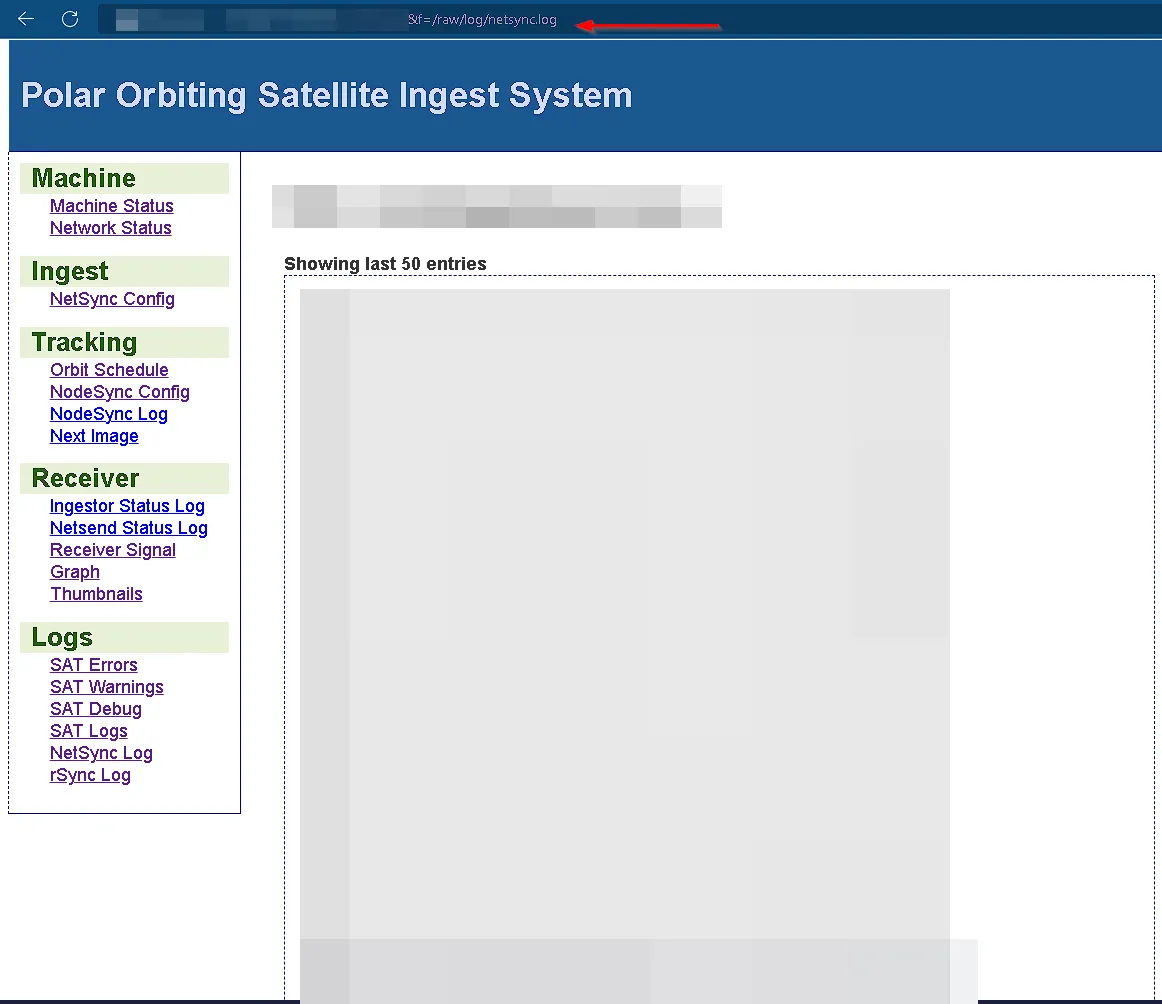
What made this particularly interesting was the real-time nature of the data. We noticed that the file associated with this parameter was constantly updating. This suggested the application wasn’t just reading static files but was actively pulling in dynamic data, likely from a system process on the server itself.
We quickly determined that the backend was running PHP on an Apache server. Our next step was to figure out how this specific function was implemented. We considered a few possibilities. One common method is using PHP’s file_get_contents() function to grab user input and display it. This can lead to vulnerabilities like Path Traversal or Server-Side Request Forgery (SSRF).
Another possibility was the include() function, which, when combined with user input, can lead to Local File Inclusion (LFI) and, in some cases, Remote Code Execution (RCE) via techniques like log poisoning.
However, a much more direct and dangerous method involves system call functions like exec(), system(), or shell_exec(). These functions run commands directly on the server’s operating system. Our tests confirmed that by injecting shell metacharacters like a semicolon (;) or double ampersands (&&), we could break out of the intended command and execute our own.
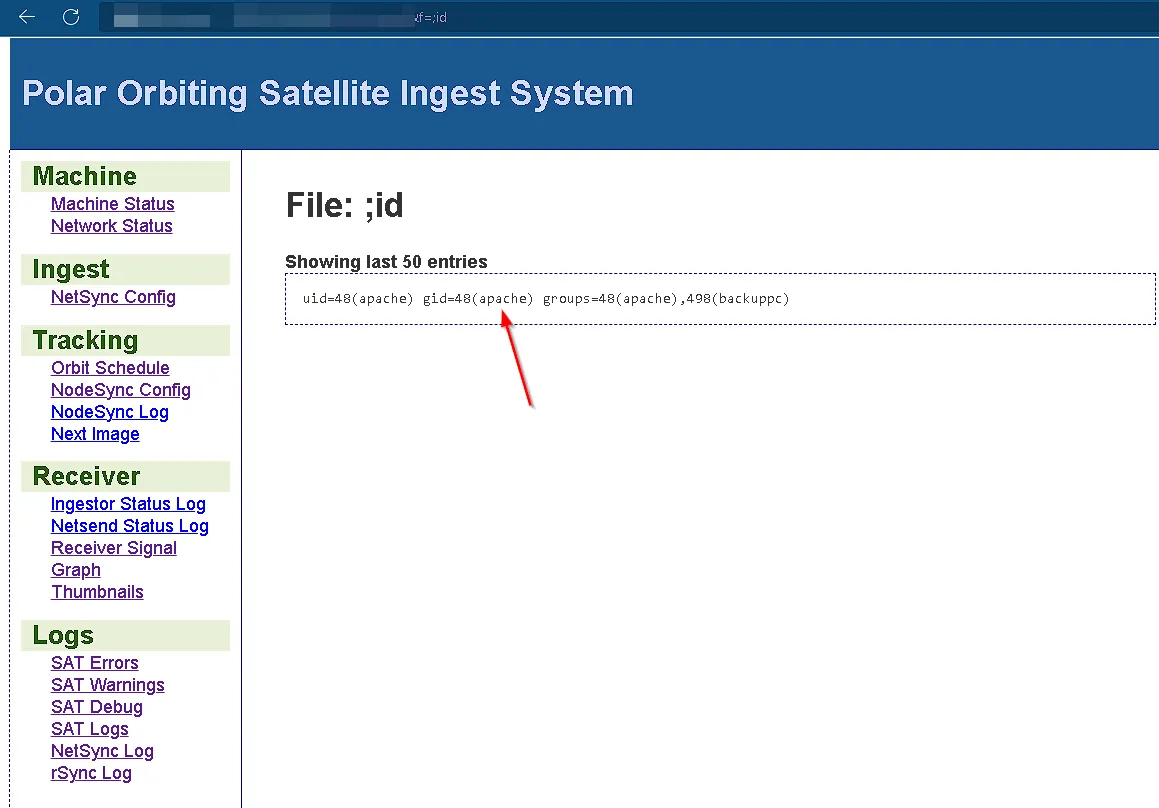
We had successfully achieved command injection.
Responsible Disclosure
Upon gaining our initial foothold, our focus shifted from exploitation to responsible disclosure. Our goal was not to cause harm, but to demonstrate the severity of the vulnerabilities and ensure the system was secured before it could be exploited by malicious actors.
We immediately compiled a detailed report of our findings, including a step-by-step breakdown of how we achieved command injection, the potential impact on the system, and our recommendations for a proper patch.
Our initial contact with the relevant government body was made on October 28th, 2022, at 11:23 AM. We were pleased to receive a prompt and professional response on November 24th, 2022. The agency was cooperative and took our findings seriously, confirming that the vulnerabilities had been patched.
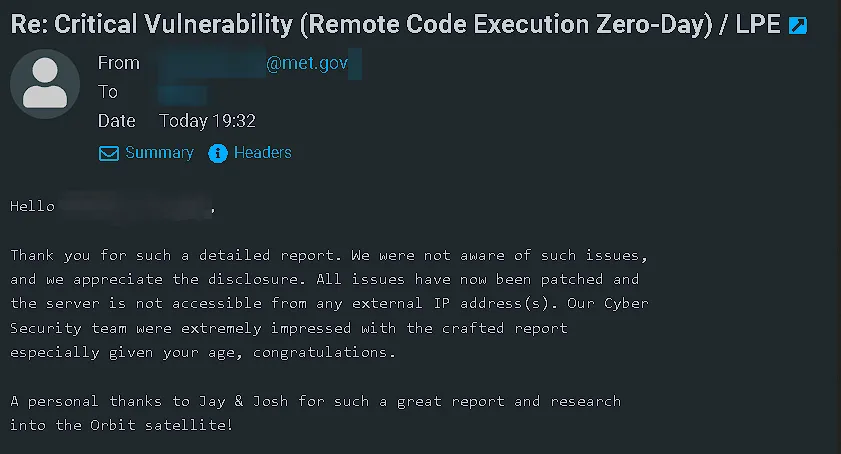
Conclusion: From Discovery to the BSides Cymru Stage
This experience was a powerful reminder of the importance of proactive security assessments and a robust vulnerability disclosure program. The journey, from a simple discovery in a public forum to the final confirmation of a patched system, was a testament to the effectiveness of ethical hacking.
Kudos to @0SPwn (James W.), @xorjosh (Josh Allman)
We were honored to share our findings and the story of this responsible disclosure at BSides Cymru 2023. Presenting our research to a community of security professionals allowed us to highlight how seemingly small clues can lead to critical discoveries and underscore the importance of securing even the most niche systems.